As an NCSC Certified Assured Service Provider and Certification Body, Adapt-IT can support Health and Care based businesses or organisations, in achieving Cyber Essentials or the IASME Cyber Assurance-based policies, processes and approach to better protect their business and clients.
Added to our unique understanding of all assistive IT and Gaming systems within a care environment Adapt-IT are well positioned to be the IT partner of choice. This allows enabling the care Industry to focus on care giving and supporting local communities.
Scroll down for more details

Business enablement: The Cyber Journey and Cycle
Working in the Care sector is tough, but protecting your business and data shouldnt be. Adapt-IT can support your organisation to put in place the ability to protect your organisation from the main threats to your business. We have a unique view of the care industry and with this experience combined with expert cyber knowledge we can support your IT in helping to ensure precious time is spent on providing your care services.
Cyber Essentials and IASME Governance is not about certification or compliance, It is about business enablement. Allowing your teams to work flexibly and in a secure and resilient way. Cyber Security is seen as a bind or something that must be done that comes at a cost. of course, a balanced and security in depth approach is going to cost both financially and in your teams time. So, it is important this is done efficiently and in a balanced way. However, if done appropriately this cost can be balanced and business efficiency can be gained.

Maintaining Focus on Care
Better Results
By using specialists to carry out the parts of Security you want managed, your business will get better results by being able to focus on your core and critical risks.
Achieve the right balance
Our specialists can help you achieve the right security balance for your business. By balancing cost and risk to meet your compliance and regulatory obligations.
Quicker deployment
Security specialists can reduce time to implementation and risk of delays and unpredictable outcomes. Our teams can either run, or supplement your team with required skills to deliver security on time.
Responsiveness
Gain the ability to improve your business’ ability to respond to any risks or threats that your business faces quickly and efficiently. Reducing impact to you and your clients. Adapt-IT can be agile and flexible and support you when you need it most.
Ready to deliver
The Adapt-IT team will be ready to help you protect your business against the growing and ever changing threat.

Cyber Essentials and the 5 Controls
Cyber Essentials is an entry level cyber certification that allows businesses to protect against the common cyber threats that all businesses face. it covers five core areas:
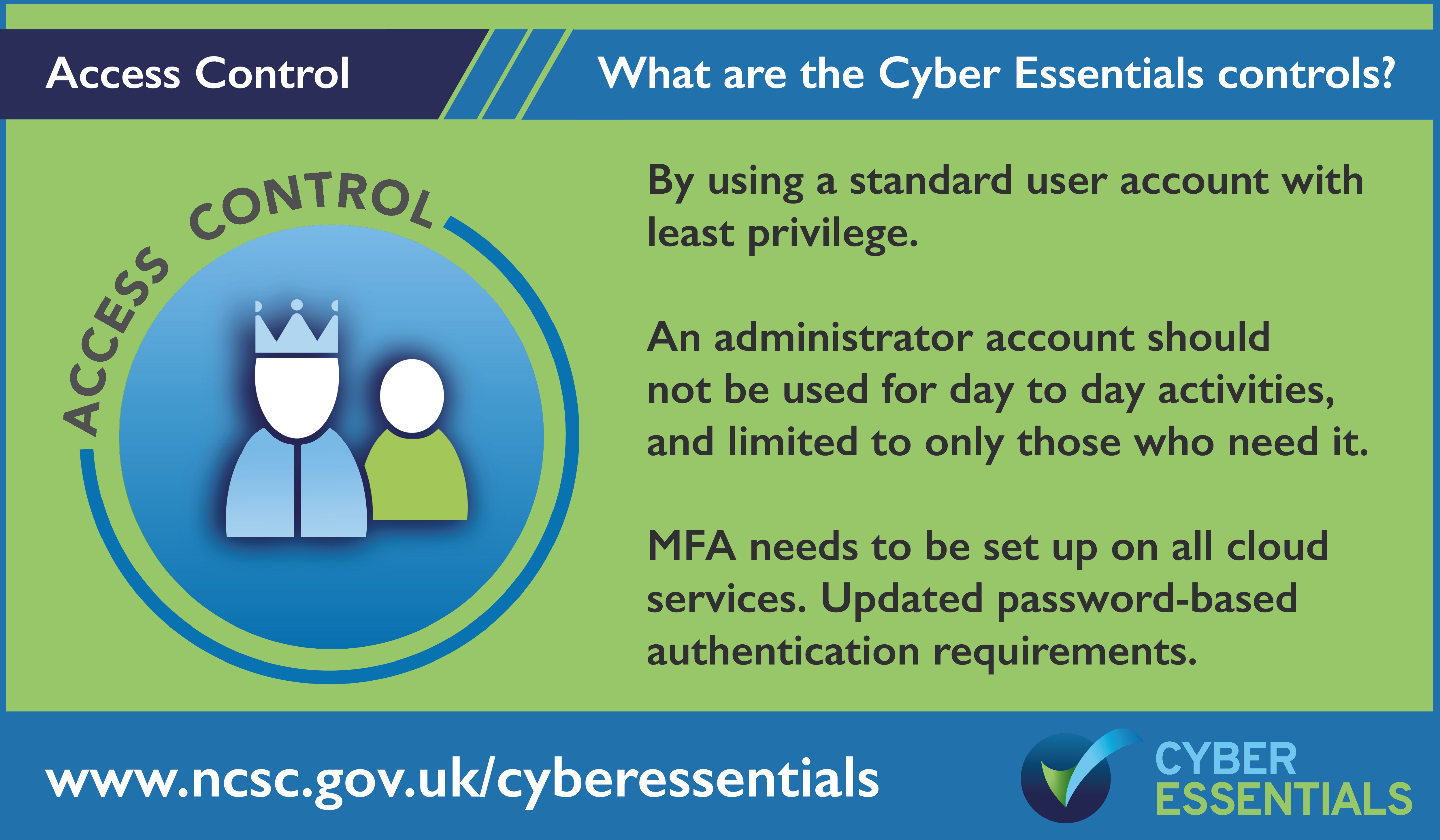
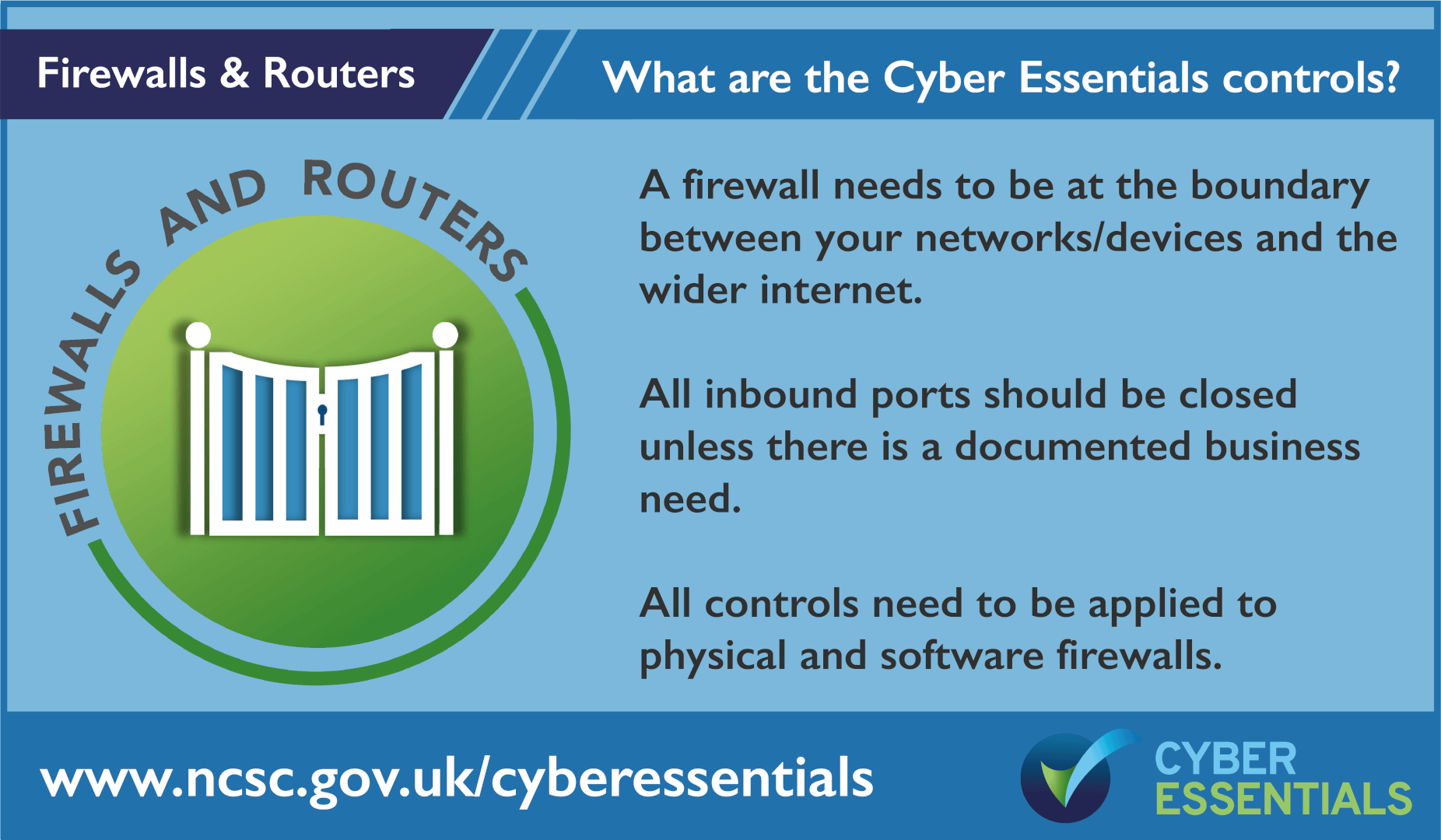
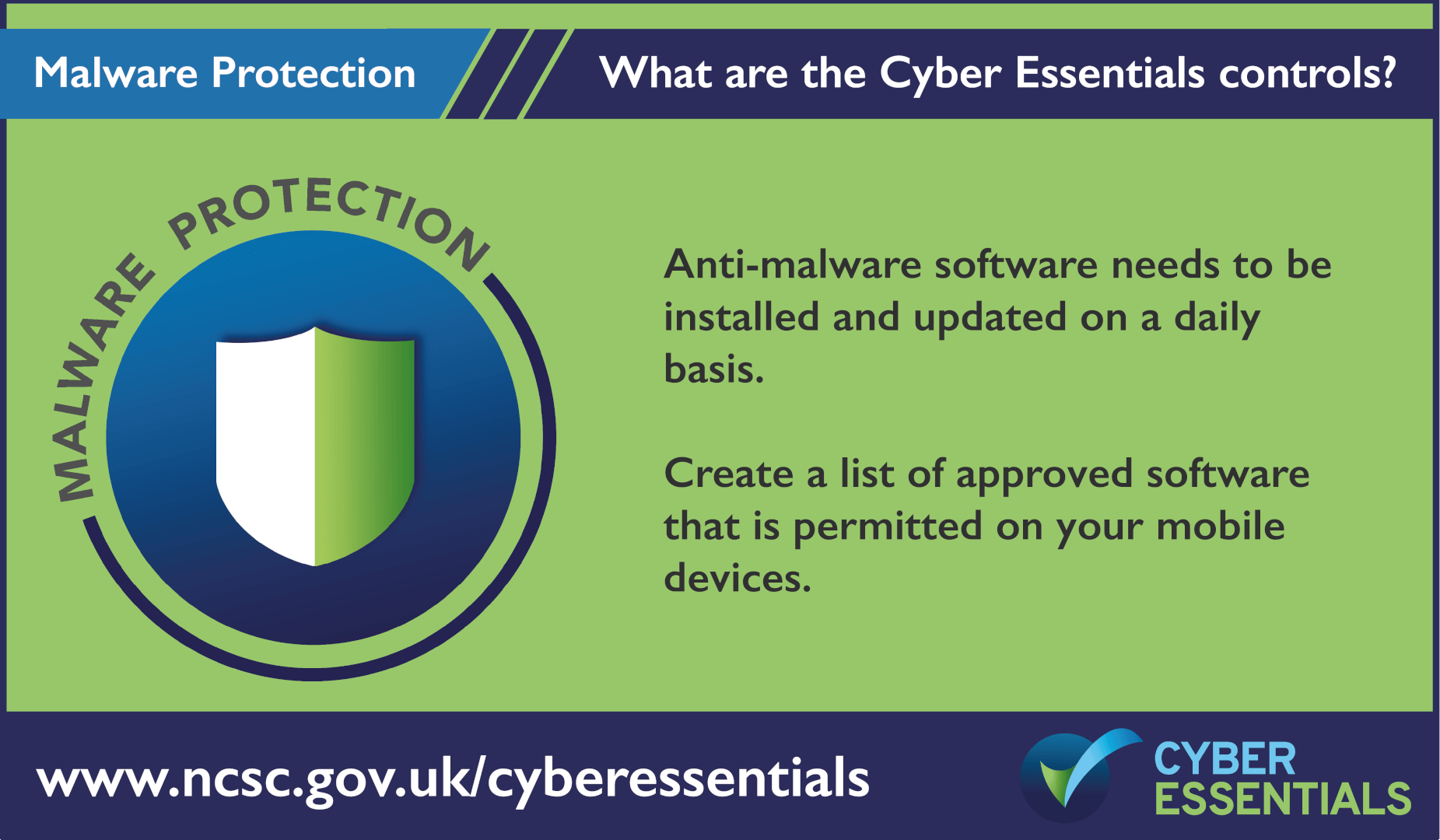
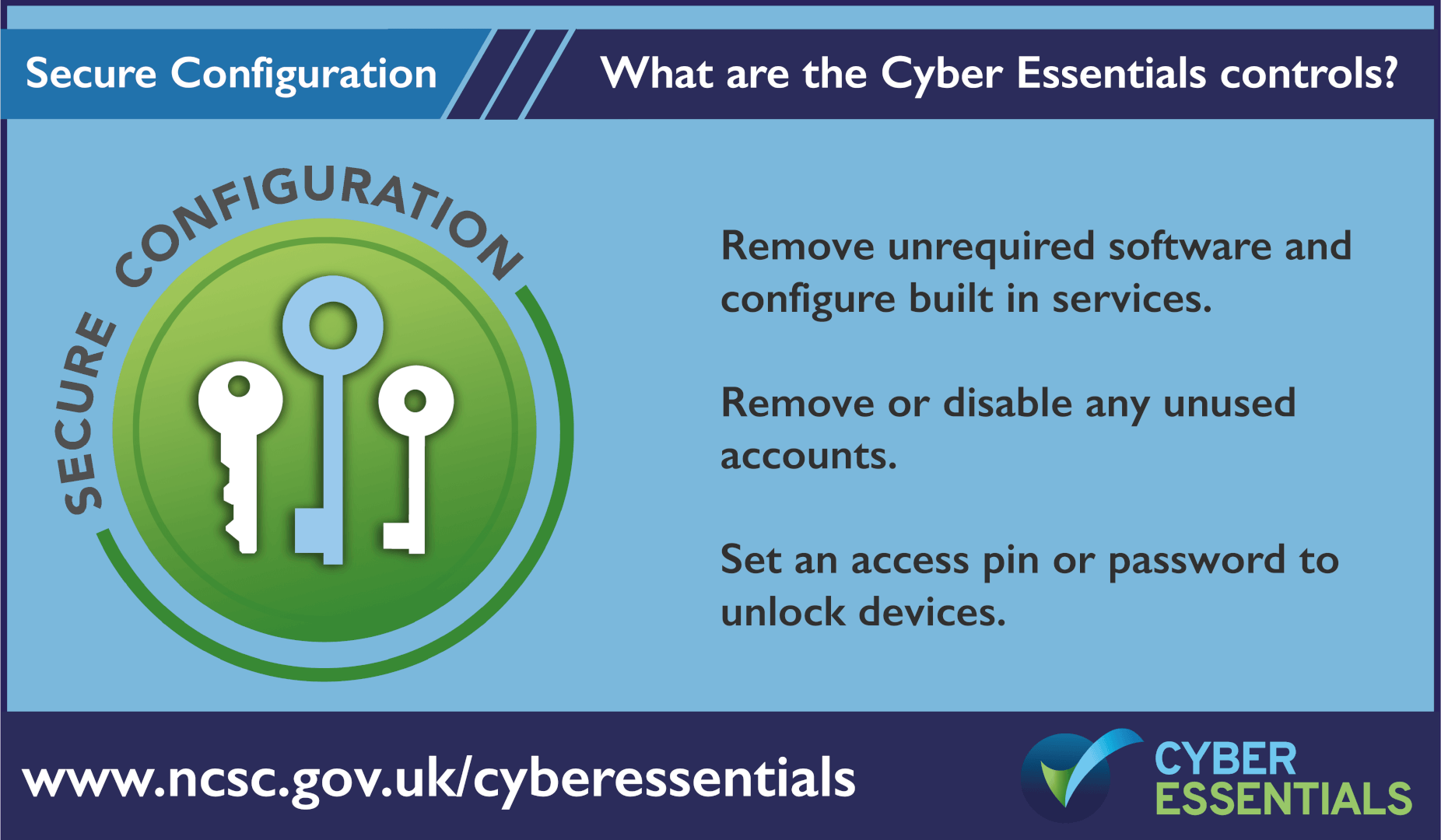
 You can download a copy of the Cyber Essentials question set by clicking
You can download a copy of the Cyber Essentials question set by clicking
Excel version here
PDF version here
You can download a copy of the NCSC Requirements for Infrastructure document that provides an overview what is needed to be Cyber Essentials ready.
PDF version here

IASME Cyber Assurance: the Next Level Certification
Important prerequisites to certification
Cyber security is a continuous journey of growth and education. IASME Cyber Assurance is not the beginning of that journey, nor is it the end. Before proceeding at this level, you will first need to demonstrate that your organisation has got the basics in place. The prerequisite for IASME Cyber Assurance certification is an up to date Cyber Essentials certification or IASME Cyber Baseline for organisations outside of the UK.
IASME is the next step in the Cyber security journey focussing on Policy, processes and overall approach to cuyber security. building on the Cyber essentials certificate it focusses on 13 core areas.
- Planning and information security
- Organisation
- Assets
- Legal and regulatory landscape
- Assessing and treating risks
- Physical and environmental
- People
- Policy and realisation
- Managing access
- Technical intrusion
- Backup and restor
- Secure business operations: Monitoring, review and change management
- Resiliance: Business continuity, incident management and disaster recovery



